FINMA Circulars 2023/1 - How resilient are you already today?

Advances in digitalization and the rapidly growing threat of cyberattacks triggered a full revision of FINMA Circular 2008/21, which is being replaced by FINMA Circular 2023/1 "Operational risks and resilience - banks". At the European level, many Swiss players in the financial services sector are required to implement the "Digital Operational Resilience Act (DORA)" by January 2025. For this European regulation, Eraneos has recently published an in-depth article.
With the revised circular, FINMA specifies supervisory practice with regards to:
- Overarching operational risk management
- ICT risk management
- Cyber risk management
- Critical data risk management
- Business continuity management (BCM)
- Management of risks from cross-border service business
In addition, the Circular includes chapters on ensuring operational resilience and the continuation of critical services during the resolution and recovery of systemically important banks.
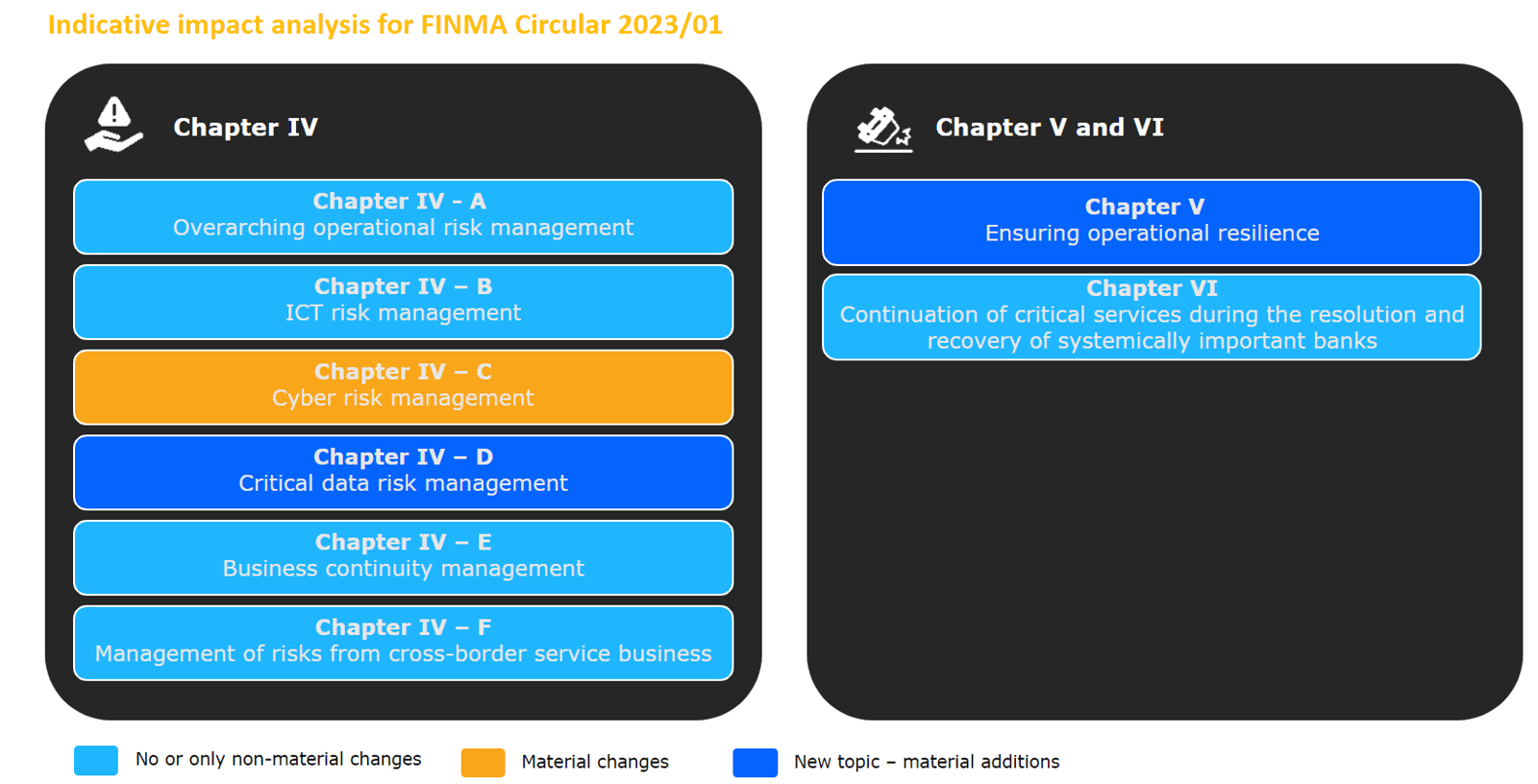
The changes in content relate to existing risk management topics as well as new topics, particularly in relation to critical data risk management and operational resilience, which require a review of the bank's control framework:
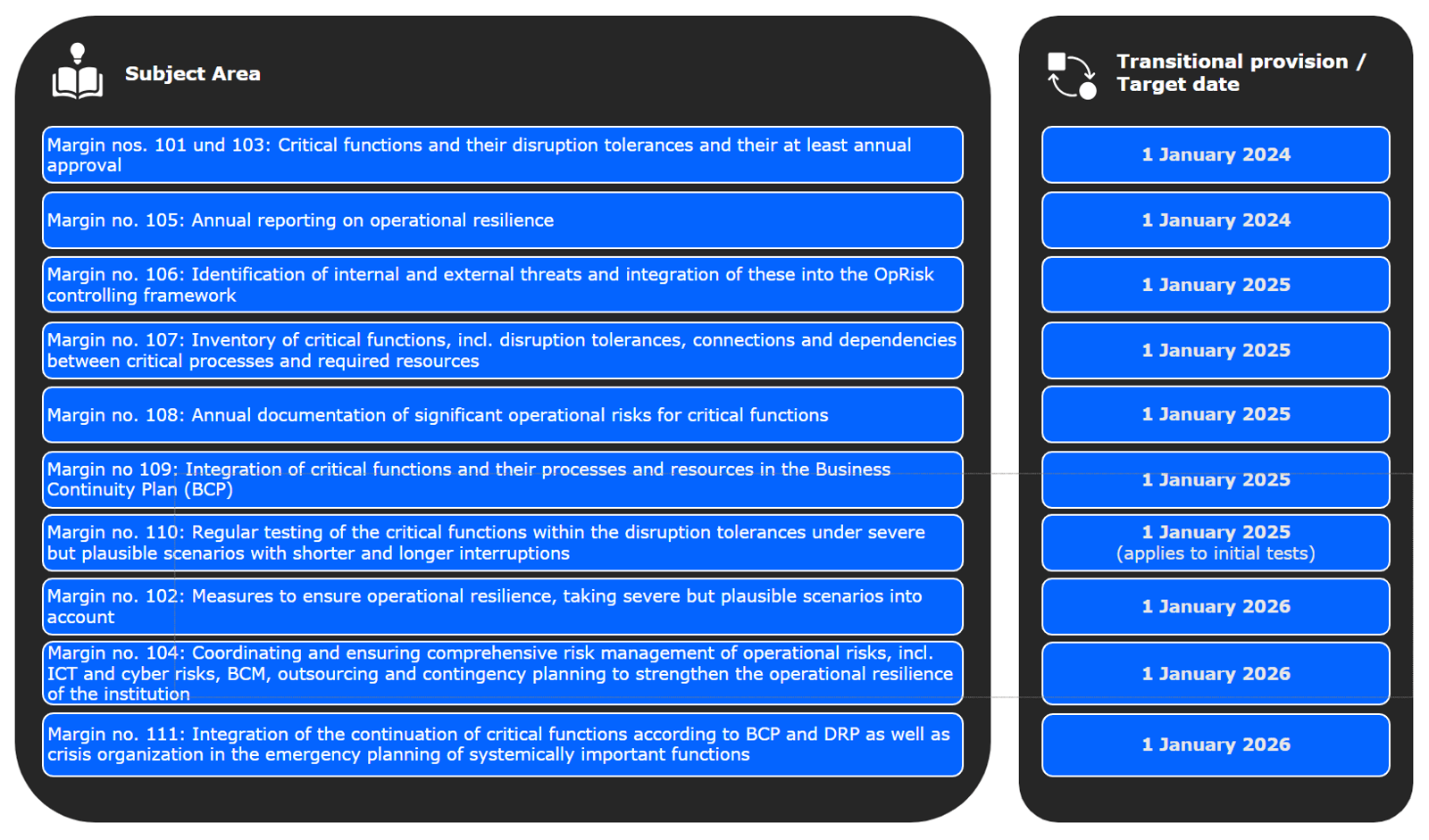
FINMA Circular 2023/1 will enter into force on 1 January 2024. However, for the requirements of the new Chapter V "Ensuring operational resilience", FINMA provides for an easing of the implementation horizon depending on the topic area, which is summarized in the following chart:
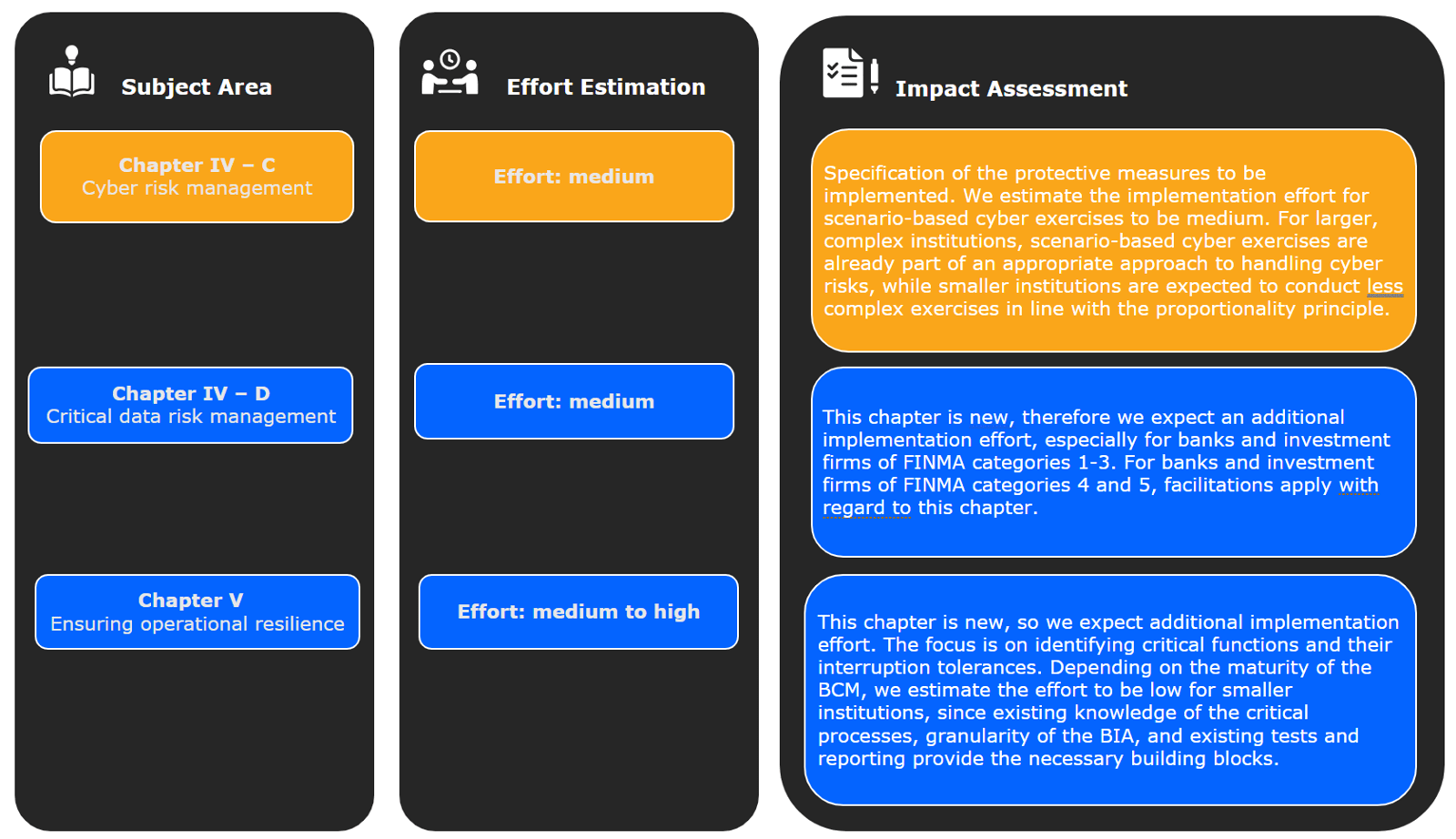
We see the ambitious timeframe for implementing the stricter requirements of Chapter IV, especially in connection with Chapter IV, point C "Cyber risk management" and Chapter IV, point D "Critical data risk management", as a major challenge.
Chapter V "Ensuring operational resilience" is new and of central importance for the implementation of the new FINMA Circular. Therefore, in our view, it represents another major challenge - even though a two-year transition period has been granted for the implementation of key components of this chapter from the time the Circular comes into force.
To meet the requirements of the Circular, we recommend implementing the following steps, among others. Please note that this is only an exemplary extract from the entire catalogue of requirements of the FINMA Circular:
- If not already implemented in your company, integrate the approval of strategies for dealing with ICT, cyber risks, critical data and BCM into the management of operational risks.
- Create an inventory of all outsourced ICT services that affect critical or important functions and ensure that this inventory is kept up to date. Place a special focus on service providers that could be considered system critical such as large cloud service providers (Amazon Web Services, Microsoft Azure).
- Have your networks and systems checked for existing vulnerabilities. We offer our customers vulnerability scans (e.g., on their website or specific applications) with a report compiled within 7-14 days for relevant target groups. The execution of penetration tests and red teaming exercises is more comprehensive. Penetration tests focus on the identification of technical vulnerabilities and a risk assessment of the identified vulnerabilities. A red teaming exercise, on the other hand, is not limited to identifying vulnerabilities in systems, but also tests organizational vulnerabilities, for example through simulated phishing campaigns and social engineering attacks. While penetration tests end with the identification of vulnerabilities, red teaming exercises also actively exploit the identified vulnerabilities.
- Organize tabletop exercises simulating a ransomware attack on systems and data. We don't just ask our clients who does what by when, but also: How do you know that the systems you back up won't be reinfected immediately? How can you be sure that your backups have not been compromised? How can you determine when the systems (and data) have been infected? How will you restore the data and systems after that time?
- Create or review existing plans for your internal and external communications in the event of an incident. These plans define, among other things, the targeted and timely communication with your customers, regulators, and business partners as well as your own employees.
Our experts have many years of experience in risk management, cybersecurity and digitalization and are prepared to answer any questions you may have. Let us strengthen your operational resilience for the future together!
Cultivate strong partnerships and networks

Kerstin Leibig
Managing Consultant
Financial Services, Telco & Utilities
+41 58 411 91 18

Andreas Rostin
Head of Cybersecurity
Financial Services, Telco & Utilities
+41 58 411 91 74

Roman Regenbogen
Head of Regulatory & Compliance
Financial Services, Telco & Utilities
+41 58 123 93 20
